Please enable JavaScript in your web browser; otherwise some parts of this site might not work properly. Scammers may try to use the internet to steal your personal information or trick you into sending them money. Learn how to stay safe online. If you believe you’re a victim of an internet-related crime, report it to these government authorities:. The Internet Crime Complaint Center IC3 will send your internet-related criminal complaint to federal, state, local, or international law enforcement. In addition to filing an IC3 complaint, contact your credit card company. Let them know about unauthorized charges or if you think your credit card number was stolen. The Federal Trade Commission FTC shares consumer complaints, including online scams with local, state, federal, and foreign law enforcement. Learn how to spot common scams and fraud. Keep your computer software updated. Download the latest versions of your operating system, web browsers, and apps. Talk to your kids about being safe and responsible online.
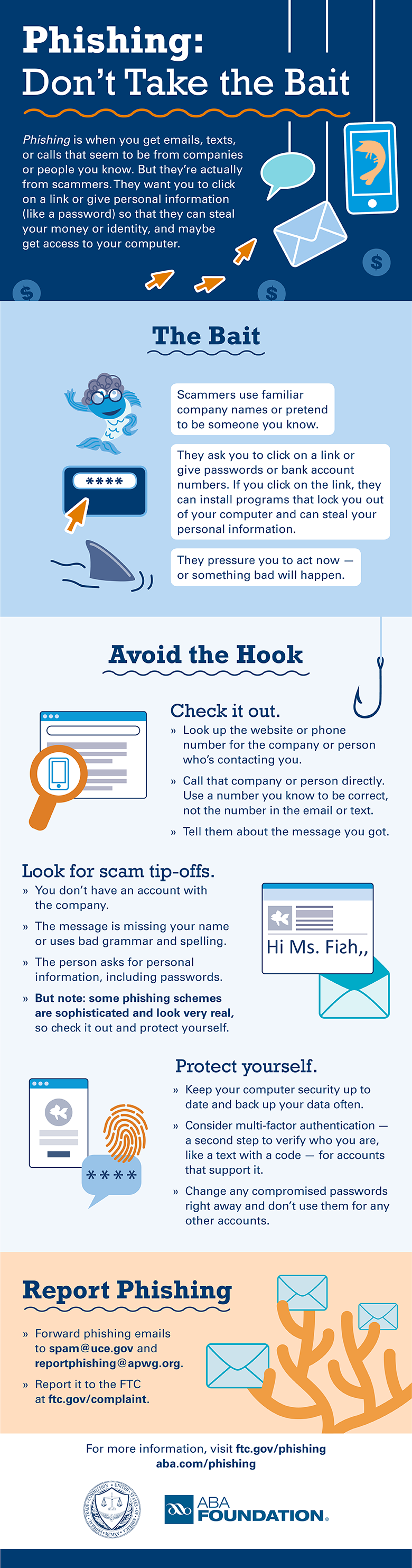
What Is Phishing?
⓫-9 -(
Misleading websites, emails and phone numbers
)}If you have a complaint about how a company is handling your personal information, click privacy concerns. The site provides streamlined checklists and sample letters to guide you through the recovery process. Visit ftc. The National Do Not Call Registry gives you a choice about whether to receive telemarketing calls at home. Most telemarketers should not call your number once it has been on the registry for 31 days. If they do, you can file a complaint at www. Your complaints help consumer protection agencies around the world spot trends and work together to prevent international scams. Mobile Devices or Telephones. Landline Telephone Devices or Services — Landline telephone devices or the services provided by a company, including billing, internet phone service and carrier switching Unwanted Text Messages — Unwanted text messages on a mobile device Something Else. Internet Services, Online Shopping, or Computers. Education, Jobs, and Making Money. Education — for-profit schools, online education, diploma programs, educational scholarships Business Opportunities, Work-at-Home Plans, Franchise or Distributorships — Business opportunities or work-at-home opportunities Job Offers — Requests for money or personal information from someone offering an employment opportunity Multi-Level Marketing or Pyramid Schemes — Sale or distribution of multi-level marketing plans, pyramid schemes, or chain letters Something Else. Credit and Debt. Credit and Loans — Credit cards, credit reporting, mortgages, pay day loans or other loan services Debt — Collection practices of a company, the services of a debt management or credit counseling company, or the actions of a company offering to repair credit Something Else. Robocalls — Recorded messages or robocalls on a landline or mobile device Telemarketing — Unwanted telemarketing calls on a landline or mobile device Text — Unwanted text messages on a mobile device SPAM — Unsolicited or fraudulent e-mails Something Else. Rip-offs and Imposter Scams Click a subcategory below to begin filing your complaint. Mobile Devices or Telephones Click a subcategory below to begin filing your complaint. Landline Telephone Devices or Services: Landline telephone devices or the services provided by a company, including billing, internet phone service and carrier switching Unwanted Text Messages: Unwanted text messages on a mobile device Something Else.⓬
On This Page
We, humans, can become an easy target for malicious actors who want to steal our most valuable personal data. Criminal minds can reach these days further than before, into our private lives, our homes and work offices. And there is little we can do about it. Source: Federal Trade Commision. For this reason, we need to know what are the most popular techniques malicious actors are using to get unauthorized access to our private information and financial data. Use the links below to quickly navigate the list of online scams you need to stay away from right now. Phishing scams continue to evolve and be a significant online threat for both users and organizations that could see their valuable data in the hands of malicious actors. The effects of phishing attacks can be daunting, so it is essential to stay safe and learn how to detect and prevent these attacks. Moreover, these emails will seem to come from an official source like bank institutions or any other financial authority, legitime companies or social networks representatives for users. You will be redirect to a fake login access page that resembles the real website. In order for their success rate to grow, scammers create a sense of urgency. After you fill in your online banking credentials, cyber criminals use them to breach your real bank account or to sell them on the dark web to other interested parties. Source: News. Probably one of the oldest and most popular Internet scams used mostly by a member of a Nigerian family with wealth to trick different people.
jaemin’s bag and shoes today!
bag : $2700
shoes : $695..it’s so cute how despite he’s using such luxury items he still hangs his bunny keychain on his bag 😭😂 pic.twitter.com/8vT2wCmUWf
— J (.◜◡◝ ) (@Ijn0423) February 1, 2020
Common Types of Fraud
Please enable JavaScript in your web browser; otherwise some parts of this site might not work properly. Scams affect every part of life. These people try to trick you out of your personal information and your money. The most common types of fraud fall under these categories:. The Financial Fraud Enforcement Taskforce and the offer overviews of other types of fraud, plus what to do if you are a fraud victim. Get the information you need to protect yourself from being a victim of the latest scam tactics:. First, file a report with your local police department. You may also contact your state consumer protection office. You can also report certain types of scams and fraud to federal enforcement agencies.
Welcome to the FTC Complaint Assistant
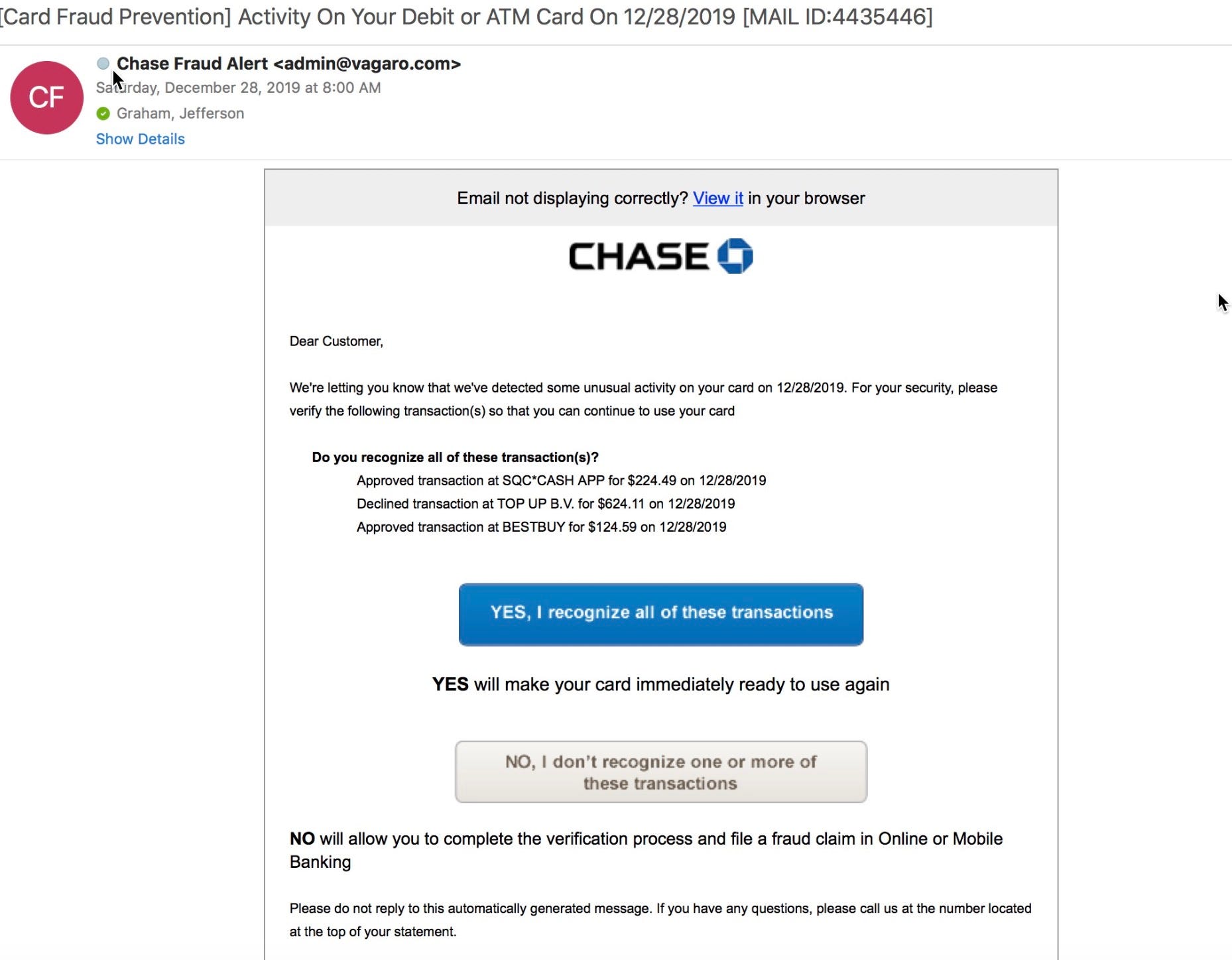
Phishing is the fraudulent attempt to obtain monej information such as usernames, passwords and credit card details by disguising oneself as a trustworthy entity in an electronic communication. Phishing is an example of social engineering techniques being used to deceive users. Users are often lured by communications purporting to be from trusted parties such as social web sitesauction siteswebsite, online payment processors or IT administrators.
Attempts to deal with phishing incidents include legislationuser training, public awareness, and technical security measures the latter being due to phishing attacks frequently exploiting weaknesses in current web security. The word itself is a neologism created as a homophone of fishing. Phishing attempts directed at specific individuals or companies have been termed spear phishing.
Threat Group Fancy Bear used spear phishing tactics to target email accounts linked to Hillary Clinton ‘s presidential campaign. They attacked more than 1, Google accounts and implemented the accounts-google. The term whaling refers to spear phishing attacks directed specifically at senior executives and other high-profile targets. The content of a whaling attack email may be an executive issue such as a subpoena or customer complaint. Clone phishing is a type of phishing attack whereby a legitimate, and previously delivered, email containing an attachment or link has had its content and recipient address es taken and used to create an almost identical or cloned email.
The attachment or link within the email is replaced with a malicious version and then sent from an email address spoofed to appear to come from the original sender. It may claim to be a resend of the original or an updated version to the original. Typically this requires either the sender or recipient to have been previously hacked for the malicious third party to obtain the legitimate email. Mojey methods of phishing use some form of technical deception designed to make a link in an email and the spoofed website it leads to appear to belong to the spoofed organization.
Many desktop email clients and web browsers will show a link’s target URL in the status bar while hovering the mouse over it. This behavior, however, may in some circumstances be overridden by the phisher.
Internationalized domain names IDN can be exploited via IDN spoofing [22] or homograph attacks[23] to create web addresses visually identical to a legitimate site, that lead instead to malicious version.
Phishers have taken advantage of a similar risk, using open URL redirectors on the websites of trusted organizations to disguise malicious URLs with a trusted domain. Phishers have sometimes used images instead of text to make it harder for anti-phishing filters to detect the text commonly used in phishing emails.
Some phishing scams use JavaScript commands in order to alter the address bar of the website they lead to. An attacker can also potentially use flaws in a trusted website’s own scripts against the victim.
In reality, the link to the website is crafted to carry out the attack, making it very difficult to spot without specialist knowledge. Such websitws flaw was used in against PayPal.
To avoid anti-phishing techniques that scan websites for phishing-related text, phishers sometimes use Flash -based websites a technique known as phlashing.
These look much like the real website, but hide the text in a multimedia object. Covert redirect is a subtle method to perform phishing attacks that makes links appear legitimate, but actually redirect a victim to an attacker’s website. The flaw reporying usually masqueraded under a log-in popup based on an affected site’s domain. This often makes use of open redirect and XSS vulnerabilities in the third-party application websites. Normal phishing attempts can be easy to spot because the malicious page’s URL will usually be different from the real site wbesites.
For covert redirect, an attacker could use a real website instead by corrupting the site with a malicious login popup dialogue box. This makes covert redirect different from. For example, suppose a victim clicks a malicious phishing link beginning with Facebook. A popup window from Facebook will websited whether the victim would like to authorize rporting app. If the victim chooses to authorize the app, a «token» will be sent to the attacker and the victim’s personal sensitive information could be exposed.
These information may include the email address, birth date, contacts, and work history. Worse still, the attacker may possibly control and operate the user’s account. This could potentially further compromise the victim.
This vulnerability was discovered by Wang Jing, a Mathematics Ph. Users can be encouraged to click on various kinds of unexpected content for a variety of technical and social reasons. For example, a malicious attachment might masquerade as a benign linked Google Doc.
Alternatively users might be outraged by a fake news story, click a link and become infected. Not all phishing attacks require a fake website. Messages that claimed to be from a bank told users to dial a phone number regarding problems with their bank accounts. Vishing voice phishing sometimes uses fake caller-ID data to give the appearance that calls come from a trusted organization. A phishing technique was described in detail in a paper and presentation delivered to the International HP Users Group, Interex.
The term «phishing» is said to have been coined by the well known spammer and hacker in the mids, Khan C Smith. Phishing on AOL was closely associated with the warez community that exchanged unlicensed software and the black hat hacking scene that perpetrated credit card fraud and other online crimes. AOL enforcement would detect words used in AOL chat rooms to suspend the accounts of individuals involved in counterfeiting software and trading stolen accounts.
Since the symbol looked like a fish, and rdporting to the popularity of phreaking it was adapted as «Phishing». AOHellreleased in earlywas a program designed to hack AOL users by allowing the attacker to pose as an AOL staff member, and send an instant message to a potential victim, asking him to reveal his password. Once the victim had revealed the password, the attacker lhihing access and use the victim’s account for fraudulent purposes. Phishing became so prevalent on AOL that they added a line on all instant messages stating: «no one working at AOL will ask for your password or phkhing information».
In lateAOL crackers resorted to phishing for legitimate accounts after AOL brought in measures in late to prevent using fake, algorithmically generated credit card numbers to open accounts.
The shutting down of the warez scene on AOL caused most phishers to leave the service. Retrieved May 5, There are anti-phishing wdbsites which publish exact messages that have been recently circulating the internet, such as FraudWatch International and Millersmiles.
Such sites often provide specific details about the particular messages. As recently asthe adoption of anti-phishing strategies by businesses needing to protect personal and financial information was low. These techniques include steps that can be taken by individuals, as well as by organizations. Phone, web site, and email phishing can now be reported to authorities, as described.
People can be trained to recognize phishing attempts, and to deal with them through a variety of approaches. Such education can be effective, especially where training emphasises conceptual knowledge [] and provides direct feedback. Many organisations run regular simulated phishing campaigns targeting their staff to measure the effectiveness of their training.
People can take steps to avoid phishing attempts by slightly modifying their browsing habits. Alternatively, the address that the individual knows is the company’s genuine website can be typed into the address bar of the browser, rather than trusting any hyperlinks in the suspected phishing message.
Nearly all webaites e-mail messages from companies to their customers contain an item of information that is not readily available to phishers. Some companies, for example PayPalalways address their customers by their username in emails, so if an email addresses the recipient in a generic fashion » Dear PayPal customer » it is likely to be reportinng attempt at phishing.
However it is unsafe to assume that the presence of personal information alone guarantees that a message is legitimate, [] and some studies have shown that the presence of personal information does not significantly affect the success rate of phishing attacks; [] which suggests that most people do not pay attention to such details.
Emails from banks and websiites card companies often include partial account numbers. However, recent research [] has shown that the public do not typically distinguish between the first few digits and the last few digits of an account number—a significant problem since the first few digits are often the same for all clients of a financial institution.
The Anti-Phishing Working Group produces regular report on trends in phishing attacks. A wide range of technical approaches are available to prevent phishing attacks reaching users or to prevent them from successfully capturing sensitive information.
Specialized spam filters can reduce the number of phishing emails that reach their addressees’ inboxes. These filters use a number of techniques including machine learning [] and natural language processing approaches to classify phishing emails, [] [] and reject email with forged addresses.
Another popular approach to fighting phishing is to maintain a list of known phishing sites and to check websites against the list. One such service is the Phihung Browsing service. Opera 9. Rporting implementations of this approach send the visited URLs to a central service to be checked, which has raised concerns about privacy. An approach introduced in mid make money reporting phihing websites switching to a special DNS service that filters out known phishing domains: this will work with any browser, [] and is similar in principle to using a hosts file to block web adverts.
To mitigate the problem of phishing sites impersonating a victim site by websitee its images such as logosseveral site owners have altered the images to send a message to the visitor that a site may be fraudulent. The image may be moved to a new filename and the original permanently replaced, or a server can detect that the image was not requested as part of normal browsing, and instead send a warning image.
The Bank of America website [] [] is one of several that asks users to select a personal image marketed as SiteKey and displays this user-selected image phijing any forms that request a password. Users of the bank’s online services are instructed to enter a password only when they see the image they selected.
However, several studies suggest that few users refrain from entering their passwords when images are absent.
A similar system, in which an automatically generated «Identity Cue» consisting of a colored word within a colored box is displayed to each website user, is in use at other financial institutions.
Security skins [] [] are a related technique that involves overlaying a user-selected image onto the login form as a visual cue that the form is legitimate.
Unlike the website-based image schemes, however, the image pjihing is shared only between the user and the browser, and not between the user and the website. The scheme also relies on a mutual authentication protocol, which makes it less vulnerable to attacks that affect user-only authentication schemes.
Still another technique relies on a dynamic grid of images that is different for each login attempt. The user must identify the pictures that fit their pre-chosen categories such as dogs, cars and flowers. Only after they have correctly identified the pictures that fit their categories are they allowed to enter their alphanumeric password to complete the login. Unlike the static images used on the Bank of America website, a dynamic image-based authentication method creates a one-time passcode for the login, requires active participation from the user, and is very difficult for a phishing website to correctly replicate because it would need to display a different grid of randomly generated images that includes the user’s secret categories.
Several companies offer banks and other organizations likely to suffer from phishing scams round-the-clock services to monitor, analyze and assist in shutting down phishing websites.
Solutions have also emerged using the mobile phone [] smartphone as a second channel for verification and authorization of banking transactions.
Organisations can implement two sebsites or multi-factor authentication MFAwhich requires a user to use at least 2 factors when logging in. For example, a user must both present a smart card and a password.
This mitigates some risk, in the event of a successful phishing attack, the stolen password on its own cannot be reused to further breach the protected. However, there are several attack methods which can defeat many of the typical systems.
How the Cash App scam actually works ( in detail) , and how to avoid Scammers
⓫-5 -(
Search form
)}Pharming and fake websites are a popular way to do this, so read on to know how you can spot them, and how you can report fake websites and pharming scams. Pharming is a scamming technique in which attackers redirect traffic of a legitimate website to another fraudulent website with the purpose of spreading malware or stealing sensitive data from victims. It looks a bit like. This fake website will look exactly the same as Facebook. Unless you’re looking for it, spotting a fake website is incredibly rpeorting. When you enter your email and password, they can see it and note reporfing. The scammer would have your name, and bank details. They could literally then just sign into your real account as you, and empty your account. How they do this is quite technical and they use several techniques to make it possible, such as DNS Cache Poisoning or compromising a host to make it possible. The best way to avoid getting pharmed is to always make sure you have a good antivirus or anti-malware installed and that it is updated regularly. This means the website has been validated by an authoritative third party to be what it claims to be. There are also a couple of other things you can look out. Monney URL might have an incorrect spelling, or have random letters or numbers before or after it. Also, while scammers do a good job at making a fake website look real, the graphics might not be hi-res and the layout might be slightly off. If you have been a victim of a pharming scam, or have spotted a fake website, there are a few steps you should .⓬
Comments
Post a Comment